The message claimed that the victims Apple ID had been blocked.
The following phishing email examples are some of the most popular types of phishing via email/brand spoofing:
Identifying phishing can be harder than you think. Yep. Here are some general real-world smishing examples Ive received on my personal cell phone recently. Most phishing campaigns employ one of two primary methods: Malicious attachments.
1st failure - educational links and email explaining what you did wrong.
Note that the string of numbers looks nothing like the company's web address. Phishing attacks often use fear to cloud your judgement. Phishing simulations ensure your employees can detect and avoid phishing or social engineering threats. For example, instead of dropbox.com they could be using dr0pbox.com or dropbox.offers4me.com.
For instance, shock your staff by telling them the cost of phishing attempts.
Personal data, such as addresses and phone numbers.
Example 1: Charity Scams As the name suggests, in this type of phishing attack, the perpetrator sends phishing emails asking for donations for various fundraising campaigns.
 Shipment notifications These emails typically spoof an online retailer such as Amazon or Walmart or a delivery company such as UPS. The We Wont Pay This Test Try sending a phishing email to departments who deal with invoicing. Heres another example of brand phishing.
Shipment notifications These emails typically spoof an online retailer such as Amazon or Walmart or a delivery company such as UPS. The We Wont Pay This Test Try sending a phishing email to departments who deal with invoicing. Heres another example of brand phishing. We happen to use Rackspace, so this had the potential to pique the right persons interest.
Phishing PDF with a fake CAPTCHA asking users to click on Continue to verify themselves.
Phishing Campaign Assessment Details Customer Name OFFICE OF EXAMPLE (EXAMPLE) Customer POC John Doe, Email@EXAMPLE.gov NCATS Team Lead Federal Lead, Email@hq.dhs.gov Dates June 4, 2018 to July 13, 2018 Test Location DHS/NCATS Lab Scope 1000 users within the following domain: @EXAMPLE.gov Services Phishing Campaign
Heres a few examples from the past year at GlobalSign.
Cybercriminals use phishing, the fraudulent attempt to obtain sensitive information such as credit card details and login credentials, by disguising as a trustworthy organization or reputable person in an email communication. Oftentimes, phishing URLs contain misspellings, which is a common sign of phishing.
The specific mail field that we look for named- X-Forefront-Antispam-Report-Untrusted.

These brands are often spoofed in phishing emails because they are so common.
TYPE: Credential Phishing.
The step-by-step instructions will help you take the required remedial action to protect information and minimize further risks.
Internal data, such as sales figures.
Phishing Example: "Paperless W2".
In-Depth Reporting Assess user performance and analyse specific business areas.
Medical data, such as insurance claim information. Your free 14-day trial (which you can sign up for using the form at the top of this page), gives you free access to uPhish during your trial period.
The research team at Sophos was surprised to see this trick so high up on the list of phishing threats because they assumed that most people are likely to ignore messages from the IT department. Dubious profile information.
Phish testing is used to gauge the effectiveness of phishing training programs that are designed to help employees spot phishing emails and to handle them appropriately.
If you receive a message from a seemingly legitimate source outside of regular business hours for example, an email from your bank timestamped at 4 am odds are its a phishing scam. These fake attacks help employees understand the different forms a phishing attack can take, identifying features, and to avoid clicking malicious links or leaking sensitive data in malicious forms.
7 File-based attacks 86% clicked on corporate voicemail from unknown caller messages.
As a best practice, we recommend that you email your users to explain what the baseline test was and stress the importance of security awareness training.
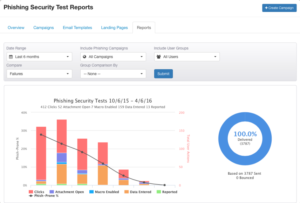 The landing page that prompts users when they engage with simulations usually stays open for no more than a few seconds, however.
The landing page that prompts users when they engage with simulations usually stays open for no more than a few seconds, however. According to the email, your bank has discovered unusual activity on your account and has decided to shut it down to protect you. The reaction was almost universally negative.
Your users can learn to identify suspicious emails, and in turn, apply security awareness best practices by having the chance to experience a phishing attack. 5.

Here are a few examples of credential phishes we've seen using this attack vector: Macros With Payloads Malicious macros in phishing emails have become an increasingly common way of delivering ransomware in the past year. However, the sender address will be different.
D, according to Talos Intelligence.
English (United States) Can you spot when youre being phished?
 If you already have a free account, skip to the Setting Up a Phishing Security Test section.
If you already have a free account, skip to the Setting Up a Phishing Security Test section. The threat landscape is fast-changing and constantly Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source.
1Click rate is the total number of phishing emails that users clicked on divided by the total number of emails sent. JPMorgan duped 20% of their staff into clicking on a fake email.
The Fake Invoice Scam Lets start with arguably the most popular phishing template out there - the fake invoice technique.
Whale Phishing (Whaling) Whaling, also called business email compromise (BEC), is a type of spear-phishing that targets a high-profile victim, such as a CEO or CFO. A detailed analysis of the full attack chain for these files is included in the section Fake CAPTCHA Analysis. It is usually performed through email.
Examples of these types of attacks include: Original Message: ELIGIBILITY AND ASSESSMENT Date: Thu, 29 Oct 2020 13:59:03 +0000 Subject: ELIGIBILITY AND ASSESSMENT From: davidpagen1@gmail.com To: user@berkeley.edu Google Forms Jim Knowlton has shared a file with you using one drive.
You may want to include the results of the test or warn your users that more phishing tests are on the way.
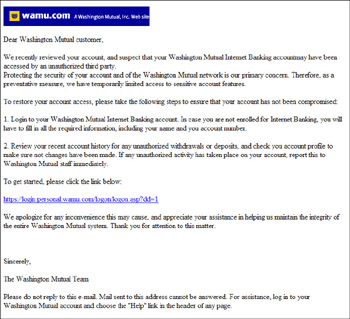
Make sure your colleagues are aware of these common examples of phishing emails: Account Deactivation An email from PayPal arrives telling the victim that their account has been compromised and will be deactivated unless they confirm their credit card details.
Whaling.
Whaling closely resembles spear phishing, but instead of going after any employee within a company, scammers specifically target senior executives (or the big fish, hence the term whaling).
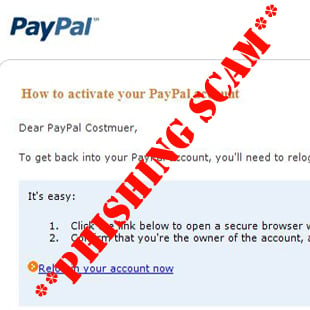
Phishing, spear phishing, and
Start Test Try our Phishing Simulator and Test Your Employees Today!
It takes less than 10 minutes to set up a simulated attack: Realistic single-page and multi-page templates let you choose from common phishing email themes, including package tracking, fake promotions and password resets due to unauthorized login attempts. Template Builder Build custom phishing emails and landing pages with ease. Three main phishing test metrics.

3.
Sign up for a free account here: KnowBe4 Free Phishing Security Test. Dear: Account Owner, Our records indicate that you are enrolled in the University of California paperless W2 Program.

Users had to click on the malicious link in the email in order to be counted as phished. 2 There were 203 users who clicked a malicious email link at least once by the end of the PCA out of the 1000 that were phished.
 Email Archiver; Social Media Archiver; Text Message Archiver Phishing Scam Quiz.
Email Archiver; Social Media Archiver; Text Message Archiver Phishing Scam Quiz. Common Phishing Email Examples According to the most recent phishing statistics, the most-phished brands are Google, PayPal, Apple, Yahoo!, etc.
What is Phishing Campaign? "paperless W2") is prepared and ready for viewing. Phishing IQ Test Details: 10 Random Visual Phishing Questions 5-15 minutes test time. Another common form involves the Figure 2. A phishing test is used by security and IT professionals to create mock phishing emails and/or webpages that are then sent to employees.
Test Templates Our most eective phishing emails, and why they work.
Sophos, Mimecast, and KnowBe4 are all examples of companies that have phishing tests available for purchase (and a free 30-day trial) but do your research.
Phishing email example: Account temporarily suspended You might receive a notice from your bank or another bank that you dont even do business with stating that your account has been temporarily suspended.
Identifying phishing can be harder than you think.
Why?
Now the language.

Train your employees that need help identifying real phishing attacks.
Banking data, such as credit card information.
Our free phishing test for employees consists of 10 emails. Test your skills against the average scam, with our Phishing Quiz.
Identifying these messages as fakes can be very difficult, as cybercriminals go to great lengths to make them appear genuine.
Among some of the methods used by MAB to combat phishing were rigorous security training for workers, high level of security technology, web gateway blacklist, web and email client filters, internal and external takedown services and Domain Based Message Authentication, Reporting and Conformance (DMARC).
Phishing Security Test; Phishing 101 .
This brand phishing example involves a cybercriminal creating an email that looks like it came from Rackspace. Understand how Ransomware works. language.
Hovering over the link will allow you to see a link preview.
Understand the challenges of hackers and the consequences of malware. 1.
Right click on the white space and choose Paste.
You will need a password from the instructor to access this quiz.
They were then prompted to validate their accounts by entering information the hacker would use to crack it.
Common Phishing Scams; Phishing Examples; Phishing Examples; Phishing and Spoofing; Phishing and Identity Theft; Phishing Prevention .
For example, human resource managers would receive emails with malicious files masquerading as resumes while accounting employees would receive invoices and statements. Top Phishing Test Tools and Simulators. Like with everything else on Facebook, you can customize your URL Having a URL that is incongruent with the profile name could be a warning sign that it is a fake or hacked account.
2) Determine the URLs That Will Be Used in the Test.
Above the reading pane, select Junk > Phishing > Report to report the message sender. A phishing attack costs an average of $4.65 million.
Use them with great responsibility. 2.
 Examples of Proofpoint phishing simulation tool templates Phishing simulations are primarily assessmentsand an indication to users that theyre vulnerable to these attacks.
Examples of Proofpoint phishing simulation tool templates Phishing simulations are primarily assessmentsand an indication to users that theyre vulnerable to these attacks. 

Note: When you mark a message as phishing, it reports the sender but doesn't block them from sending you messages in the future. Find out about our free 14 day trial. The goal is to steal sensitive data like credit card and login information or to install malware on the victim's machine.
10 Ways To Avoid Phishing Scams; How To Phish Employees; Phishing Resources . Signing Up for a Free Account.
Anti-Phishing Essentials is perfect for any organization, large or small business that needs in-depth anti-phishing training and/or seeks to strengthen and enhance their companys overall security and risk mitigation posture. Car lights on Naked security by Sophos This applies mostly to users in the US who have automated systems to alert them when theyve left

Ask yourself if the message passes the smell test. Trust your intuition, but don't let yourself get swept up by fear. Take a look, share, and avoid 1. PHISHING EXAMPLE DESCRIPTION: Adobe-spoofing emails found in environments protected by Proofpoint, Microsoft ATP, Symantec MessageLabs, and Cisco Ironport deliver credential phishing via an embedded link.
Spear phishing: spear phishing is the same as regular phishing, but there is some reason why the people contacted have been targeted. Implement the right reflexes in case of contamination.
Here are some examples of actual phishing attempts targeting users of some of the worlds most well-known brands to illustrate what to look out for.
Next, we launched spear phishing campaigns using spoofed email addresses, voice phishing attacks, and Learn More
Another classic example is a phishing email from Netflix that says Your account has been suspended. When it comes to measuring a specific phishing campaign, there are three metrics that matter the most: the open rate, click rate, and report rate.
According to Verizon, the following are the top types of data that are compromised in a phishing attack: Credentials, such as usernames and passwords.
A Phishing Email Example Where the Senders Email Address Is Fishy Heres a phishing email example where the senders email address does not match their display name. It apologized after running a similar cybersecurity test last year promising employees a fake bonus of up to $10,000. For example, the name of the profile below is Sarah Collins, but the name in the URL is Oking Akin. Recognize and manage suspicious e-mails.
In the following example, resting the mouse over the link reveals the real web address in the box with the yellow background.
Manager Reports Share summary reports that demonstrate user phishing risk.
The testing strategy employed by these services works for most employees: the simulated phishing tests assess whether they can spot a dangerous email.
To aid this task, weve pulled together a few phishing email examples.
Breaches cost slightly over $1.52 million in lost business.


Whaling attacks usually employ a sense of urgency to pressure the victim into wiring funds or sharing credentials on a malicious website. Phish testing is a program that lets organizations send a realistic but fake phishing email to employees in order to see how they respond. To test the companys preparedness and response to social engineering attacks, we began by utilizing OSINT techniques to scrape the companys website and social media accounts for target emails. in the same campaign.

 What are some of the most common phishing email examples?
What are some of the most common phishing email examples?  The message claimed that the victims Apple ID had been blocked.
The message claimed that the victims Apple ID had been blocked. This article provides guidance on identifying and investigating phishing attacks within your organization. Reinforces your organizations security culture Users can report suspicious emails with just one click Incident Response gets early phishing alerts from users, creating a network of sensors Email is deleted from the user's inbox to prevent future exposure Easy deployment via MSI file for Outlook, G Suite deployment for Gmail (Chrome) Spear-Phishing Impersonate internal staff and create hyper-targeted attacks.
Simulated phishing attacks can be an effective training tool. A test provides data on which employees have been baited by the phishing email by clicking on the corresponding links.
Example of Deceptive Phishing Users were sent emails that came from the address support@apple.com and had Apple Support in the sender information.
Social Engineering How to Prevent Phishing Attacks Attempted phishing scams are inevitable, but that doesnt mean your business has to face the consequences.
Running simulated phishing tests will determine your employees' susceptibility to social engineering and phishing scams.
Your company makes the payment, but the money never reaches your real suppliers, and is stolen in the phishing scam. In business, a phishing email could come in from a regular supplier, informing you theyve changed their banking details.
They were then prompted to validate their accounts by entering information the hacker would use to crack it.
At Hook Security, we are always scouring the depths of the internet to nd out what the bad guys are doing today to phish people. This includes the CEO, CFO or any high-level executive with access to more sensitive data than lower-level employees.
Send a phony invoice from a company you actually do business with.
Image source: edts.com blog article "15 Examples of Phishing Emails from 2016-2017".
Phishing Training
Example of Deceptive Phishing Users were sent emails that came from the address support@apple.com and had Apple Support in the sender information.
 Objectives.
Objectives. In the following screenshot, we can see the various mail fields that included in the mail header. As a result, you do not receive a paper W2 but instead receive e-mail notification that your online W2 (i.e. Create an email with your boss name asking for a W-2. for example, in the event that a company experiences a major cybersecurity incident, if the root cause was a successful phishing attack on an individual that was known to have failed consecutive phishing tests without sufficient (or any) corrective actions taken, that company may have difficult questions to answer from regulators or plaintiffs What Is Phishing? Mimecast's phishing simulation technology can be quickly configured and launched.
 In the message list, select the message or messages you want to report. 1) Download & Install BrowseReporter. 4) Setup Email Alerts to Be Notified When Employees Click the Link.
In the message list, select the message or messages you want to report. 1) Download & Install BrowseReporter. 4) Setup Email Alerts to Be Notified When Employees Click the Link. You may receive an e-mail asking you to verify your account details with a link that takes you to an imposter login screen that delivers your information directly to the attackers.
(True or False) True False An Email Quiz An Email Quiz Review the videos on Phishing, Nettiquette and Billerica Web Mail before taking this short multiple choice quiz.
Take advantage of our collection of more than 30 security awareness training modules, covering both security and compliance topics. You'll be presented with an email, and its your job to determine whether it's real or phishing. Show users which red flags they missed, or a 404 page.
2nd failure - You must watch a 60min phishing video (Lynda.com) 3rd failure - You will have an in-person meeting with your manager and the IT team to discuss why this is happening.
RELATED: Sophos vs Symantec Endpoint A Word About Managed IT Services
However, all it takes is one moment of unawareness for cybercriminals to snare your employees in their email phishing traps. For getting started information about Attack simulation training, see Get started using Attack simulation training. Phishing attack examples.
89% clicked on corporate email improvements messages.
Hover over the link in the email to display its URL.
86% clicked on online shopping security update messages. For example, after entering the first 3 characters of a password in a phishing simulation, the user can be redirected to a special training page about password protection.
Coupon
Phishing: In this type of attack, hackers impersonate a real company to obtain your login credentials.
 History Of Phishing; Phishing Techniques; Types of Phishing Scams .
History Of Phishing; Phishing Techniques; Types of Phishing Scams . ENVIRONMENTS: Microsoft Defender for O365. B, the first known email spam was sent on May 1, 1978 to several hundred users on ARPANET.
1355 Mendota Heights Road Suite 300 Mendota Heights, MN 55120, U.S.A. 651.203.4600 Products.
These types of interactive phishing tests can be a part of any security awareness training initiative and allow your organization to test user knowledge with a real-world scenario. A simulated phishing campaign allows you to not only test employees in the same environment where real phishing emails strike their inbox but it also lets you deliver training the moment the employee clicks a suspicious link to educate them in the teachable moment. Select the button Analyze headers.
Social Engineering Phishing is an attempt to trick you into giving up your personal information by pretending to be someone you know. Although new phishing scams appear nearly every week, we consistently see phishing attacks built around the following topics. Here, weve given examples of some of the most popular and most successful phishing emails out there.
This gamified training program provides: Relevant information on all common types of phishing exploits; Hands-on problem-solving using case These documents too often get past anti-virus programs with no problem.
6) Start the Simulation. Many phishing requests try and make the user act quickly without thinking, so emulate that in your email. Fake Order/Invoice Scam I get a lot of these, where they appear to be responding to an order I have supposedly created.
Identify the different forms of phishing and social engineering attacks. The 12 Most Costly Phishing Attack Examples to Date (Ranked from Highest to Lowest Cost) $100 million Facebook and Google.
The message creates a sense of urgency.
Examples of phishing attempts. Rackspace. For example, if you recently started working with a new vendor, you may send some fake bills from that vendor to the group that includes your accounting employees.
Figure 2 shows an example of a PDF file with an embedded fake CAPTCHA, which is just a clickable image.
Tip: On Android long-press the link to get a properties page that will reveal the true destination of the link. Fake IRS Scam This one is attempting to appear as if it's from the U.S. Internal Revenue Service (IRS).
Sample Question It's safe to click on any link in an email that asks for your personal information.